Azure Disk Encryption is a new capability that helps you encrypt your Windows and Linux IaaS virtual machine disks. Azure Disk Encryption leverages the industry standard BitLocker feature of Windows and the DM-Crypt feature of Linux to provide volume encryption for the OS and the data disks. The solution is integrated with Azure Key Vault to help you control and manage the disk-encryption keys and secrets in your key vault subscription. The solution also ensures that all data on the virtual machine disks are encrypted at rest in your Azure storage.
We have two option available to Encrypt VM.
- Using Storage Service Encryption (SSE) for data at rest.
- Using Azure virtual machine disk encryption (Bit locker).
Its best to enable SSE on storage level and data will be encrypted on rest but some time client demand to encrypt VMs disk as well, so we need to enable disk encryption.
Disk Encryption scenarios
The Azure Disk Encryption solution supports the following customer scenarios:
- Enable encryption on new IaaS VMs created from pre-encrypted VHD and encryption keys
- Enable encryption on new IaaS VMs created from the supported Azure Gallery images
- Enable encryption on existing IaaS VMs running in Azure
- Disable encryption on Windows IaaS VMs
- Disable encryption on data drives for Linux IaaS VMs
- Enable encryption of managed disk VMs
- Update encryption settings of an existing encrypted premium and non-premium storage VM
- Backup and restore of encrypted VMs
The solution supports the following scenarios for IaaS VMs when they are enabled in Microsoft Azure:
- Integration with Azure Key Vault
- Standard tier VMs: A, D, DS, G, GS, F, and so forth series IaaS VMs
- Enable encryption on Windows and Linux IaaS VMs and managed disk VMs from the supported Azure Gallery images
- Disable encryption on OS and data drives for Windows IaaS VMs and managed disk VMs
- Disable encryption on data drives for Linux IaaS VMs and managed disk VMs
- Enable encryption on IaaS VMs running Windows Client OS
- Enable encryption on volumes with mount paths
- Enable encryption on Linux VMs configured with disk striping (RAID) using mdadm
- Enable encryption on Linux VMs using LVM for data disks
- Enable encryption on Linux LVM 7.3 for OS and data disks
- Enable encryption on Windows VMs configured with Storage Spaces
- Update encryption settings of an existing encrypted premium and non-premium storage VM
- Backup and restore of encrypted VMs, for both no-KEK and KEK scenarios (KEK – Key Encryption Key)
- All Azure Public and AzureGov regions are supported
The solution does not support the following scenarios, features, and technology:
- Basic tier IaaS VMs
- Disabling encryption on an OS drive for Linux IaaS VMs
- Disabling encryption on a data drive if the OS drive is encrypted for Linux Iaas VMs
- IaaS VMs that are created by using the classic VM creation method
- Enable encryption on Windows and Linux IaaS VMs customer custom images is NOT supported.
- Integration with your on-premises Key Management Service
- Azure Files (shared file system), Network File System (NFS), dynamic volumes, and Windows VMs that are configured with software-based RAID systems
Few Important Points to note before implementation of VM Disk Encryption
- There is no additional charge for encrypting VM disks with Azure Disk Encryption.
- VM encryption might increase data, network, or compute resource usage, resulting in additional license or subscription costs.
- Azure use Bit locker Encryption to encrypt Azure IAAS VMs through extension.
- File Recovery (File/folder) restore is currently not supported for encrypted VMs.
- One Key vault on each region where your VMs are running and you want to encrypt VMs.
- There are three way to encrypt VM Disks (all disk, OS disk only, data disk only).
- Once you enabled disk encryption one more volume will be attached (BEK volume) which stored all decryption key locally.
- We can’t directly restore Encrypted VM first restore disks and create VM using restored encrypted disks.
- Disable encryption disables encryption of the OS, the data volume, or both on the running Windows IaaS VM. You cannot disable the OS volume and leave the data volume encrypted.
- VM required reboot during encryption and decryption or update encryption setting for non-premium storage VM.
- We can’t update encryption settings of an existing encrypted premium storage VM.
- Enabling encryption for VM Disk is risky and need proper planning and expertise.
PowerShell and Templates can be used to enable disk encryption but as of now you can’t enable encryption using Portal also in this article I used Powershell mostly.
1. Obtain Azure disk encryption prerequisites configuration script.
- Use this link to download Azure Disk Encryption Prerequisites Configuration Script.
- Copy all data and save file in Anyname.ps1 file to proceed further.
- Open the .ps1 file in Windows PowerShell ISE.
2. Run the Azure disk encryption prerequisites PowerShell command.
This PowerShell Script will first create AAD service principle and then key vault to store BEK files. Azure Disk Encryption Prerequisites script will ask you for the following information after you start the script,
- Resource Group Name (New or Existing)
- Key Vault Name (New or Existing)
- Location (where your VMs running)
- Azure Active Directory Application Name (New or Existing)
- Subscription ID (ID of subscription)
The output of the script should look something like the screen below:
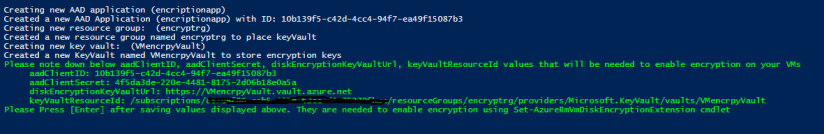
Important: – The script runs and when complete it will ask you to copy the values of the aadClientID, aadClientSecret, diskEncryptionKeyVaultUrl, and keyVaultResourceId. Copy each of these values to the clipboard and paste them into Notepad.
3. Encrypt the Azure virtual machine
You are now ready to encrypt your virtual machine, Define Variable and run below command.
$resourceGroupName = <’Virtual_Machine_RG’>
$vmName = <’your_vm_name’>
Set-AzureRmVMDiskEncryptionExtension -ResourceGroupName $resourceGroupName -VMName $vmName -AadClientID $aadClientID -AadClientSecret $aadClientSecret -DiskEncryptionKeyVaultUrl $diskEncryptionKeyVaultUrl -DiskEncryptionKeyVaultId $keyVaultResourceId -VolumeType All
Please note in –VolumeType you have below three option to define.
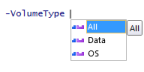
Your VM is encrypted with BEK-only but if you wanted to configure it with recovery vault for backup than BEK + KEK both required than skip steps 3 Move to next section.
Backup and restore of encrypted VMs is supported for both Windows and Linux VMs.
4. Enable VM for Backup
- Go to Keyvault that was created earlier through powershell.
- In Setting click on Keys and add a new Key for Backup (KEK Key), make sure this should be enable.
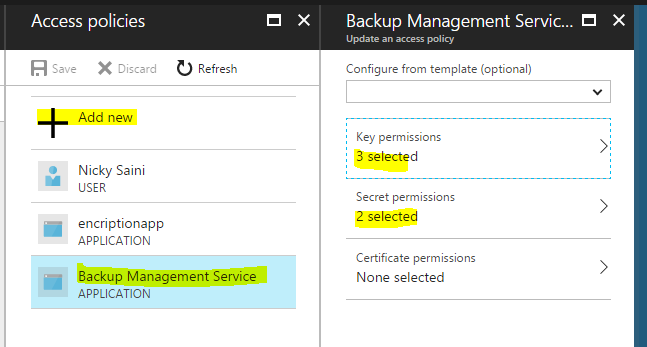
3. Go to Access Policy and give access to backup management service principle for access BEK and KEK Keys.
Key Permission- backup, get, list
Secrets Permission- get, list
4. Run the below Powershell script after defining variables.
### Define Variables
$vmName = ‘VM Name’
$resourceGroupName = “RG Name”
$adClientID = “Take from output of prerequisites configuration script”
$aadClientSecret = “Generated on step 2 of (Enable VM for Backup)”
$diskEncryptionKeyVaultUrl = “Take from output of prerequisites configuration script”
$KeyVaultName = “Take from output of prerequisites configuration script”
$keyEncryptionKeyName = ‘Take from output of prerequisites configuration script’
$keyVaultResourceId = “/subscriptions/subscription ID/resourceGroups/encryptrg/providers/Microsoft.KeyVault/vaults/keyvaultname”
$keyEncryptionKeyUrl = (Get-AzureKeyVaultKey -VaultName $KeyVaultName -Name $keyEncryptionKeyName).Key.kid
## Assign permission to AAD Service Principal(AAD APP ID)
Set-AzureRmKeyVaultAccessPolicy -VaultName $KeyVaultName -ServicePrincipalName $aadClientID -PermissionsToKeys all -PermissionsToSecrets all -ResourceGroupName $resourceGroupName
## Update encryption policy to configure backup
Set-AzureRmVMDiskEncryptionExtension -ResourceGroupName $resourceGroupName -VMName $vmName -AadClientID $aadClientID -AadClientSecret $aadClientSecret -DiskEncryptionKeyVaultUrl $diskEncryptionKeyVaultUrl -DiskEncryptionKeyVaultId $KeyVaultResourceId -KeyEncryptionKeyUrl $keyEncryptionKeyUrl -KeyEncryptionKeyVaultId $KeyVaultResourceId -VolumeType All
##Check the status once encryption is enabled
Get-AzureRmVmDiskEncryptionStatus -ResourceGroupName $resourceGroupName -VMName $vmName
Conclusion- Enabling VMs disk encryption is good option and depending on client needs. Required proper planning and expertise, if something not followed properly there are might chance you can loss that VM also recovering encrypted VM disk required lot of efforts and time.
Reference has been taken from below Microsoft article.
Good job Nicky.
LikeLike
very interesting points you have mentioned, appreciate it for posting.
LikeLike